ISCTF2025 部分题WP
SIGNIN
Ez_Caesar
题目描述:小蓝鲨看你们牢底坐穿决定送你们一点分。
下载附件:
def variant_caesar_encrypt(text): |
是简单的凯撒编码,直接在原来基础上编写decrypt函数:
def variant_caesar_decrypt(ciphertext): |
小蓝鲨的RC4系统
题目描述:送都送了,再给一个。
下载附件:
import hashlib |
得到是RC4流密码加密,
RC4的加密和解密用的为同一个函数(异或操作为自反的),所以解密只需把密文从十六进制转成字节,再调用crypt,
exp:
import hashlib |
MISC
Guess!
题目描述:这是一个经典的猜数字,开始你的数字解密之旅吧!
下载附件,是pyinstaller处理后的MiscNumberChallenge.exe,用unpack.py解包后得到extracted目录
找到misc_challenge.pyc文件,在 https://pylingual.io/ 反编译.pyc文件:
import random |
容易得到,flag编码为base64,解码即得flag:ISCTF{9ueSs_thE_@n$weR}
REVERSE
ezzz_math
题目描述:来解方程吧
IDA中打开,可疑点_main函数:
{ |
逻辑就是输入23字节字符串,用0xC(12)异或,最后将异或完的数组传给sub_401000验证。
所以,我们看向sub_401000函数:
BOOL __cdecl sub_401000(char *a1) |
可以看到,这一大长串包含了22个等式,对a1[0]到a1[22]共23个变量进行了约束,
值得注意的是:
*a1其实就是a1[0],第一个变量a1[i] << 6 = 64 * a1[i](左移6位实际上就是*64)
根据_main函数的汇编代码,得到是z3算法,
编写最终的EXP:
from z3 import * |
ezpy
题目描述:这是什么库?没见过呢
下载附件,是pyinstaller处理的ezpy.exe,按照之前做法,得到extracted文件夹,
反编译ezpy.pyc得到:
try: |
没什么用,继续找。在目录里看到了mypy.cp313-win_amd64.pyd,想着用IDA反编译试试…
在IDA中,Shift+F12看到RC4 flag checker module,得到是RC4加密,
通过一个一个函数查看的艰难寻找,在sub_36F4D1519函数中得到RC4加密的密钥ISCTF2025:
{ |
生成RC4的S-box,写入v8[i],然后执行cipher[i] = plain[i] XOR RC4_next()。
查看汇编代码,得到byte_36F4D4050的数据:
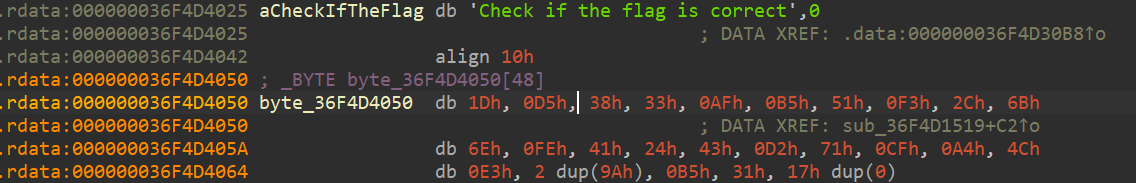
最终的EXP:
cipher = bytes([ |
MysteriousStream
题目描述:小曲冒着生命风险,读入了一个神秘的 payload.dat文件,为了不枉费小曲的艰辛……,你能逆向出被加密的秘密吗?
下载附件,包含challenge和payload.dat文件,定位至main函数:
{ |
使用key = v11[7 : 7 + 10] = "Secr3tK3y!"加密,对payload (v7) 做RC4加密,
然后循环异或key_xor = v11[0:7] = b"P4ssXOR"和v7[i] = v7[i] XOR key_xor[i % 7],
再看xor_cycle函数:
{ |
和rc4_variant函数:
{ |
变种的RC4加密逻辑为j = (j + S[i] + key[i % keylen] + (i & 0xAA)) mod 256,解密只需逆着来即可。
所以,最终的加密逻辑为cipher = XOR( RC4_variant(plaintext, key="Secr3tK3y!") , key="P4ssXOR")。
EXP:
def rc4_variant_crypt(data: bytes, key: bytes) -> bytes: |
CRYPTO
easy_RSA
题目描述:我们的爱情像欧拉函数φ(n)——无限趋近却永远达不到n的完美互质,最终只剩周期性的怀念在模n的世界里循环证明
下载加密代码:
from Crypto.Util.number import * |
是RSA中的共模攻击,m = c1 ^ s1 * c2 ^ s2 mod N,
得到EXP:
from Crypto.Util.number import long_to_bytes, inverse |
小蓝鲨的LFSR系统
题目描述:”小蓝鲨是海洋情报局的新晋密码专家,它设计了一个基于LFSR的流密码系统来加密机密信息。这个系统看起来简单高效,但小蓝鲨不知道的是,LFSR在某些情况下可能存在安全隐患。 一天,小蓝鲨的加密系统被神秘的黑客组织””深海幽灵””入侵,他们截获了一段加密信息。作为海洋安全部门的成员,你需要分析这个加密系统,找出潜在的弱点,并解密被截获的信息。”
打开附件:
import secrets |
和对应的输出文件:
initState = [0, 1, 0, 1, 1, 0, 0, 1, 1, 0, 0, 0, 0, 1, 0, 0, 1, 0, 0, 0, 1, 1, 1, 0, 0, 1, 1, 0, 1, 1, 0, 1, 0, 0, 1, 0, 1, 0, 1, 0, 0, 1, 0, 1, 1, 0, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 0, 1, 0, 0, 1, 1, 0, 1, 0, 1, 0, 0, 0, 0, 0, 1, 1, 0, 1, 0, 1, 0, 0, 0, 1, 1, 1, 1, 1, 1, 1, 0, 1, 1, 0, 1, 0, 1, 0, 0, 1, 1, 1, 1, 0, 0, 1, 1, 1, 1, 0, 1, 0, 1, 1, 0, 1, 0, 0, 0, 0, 0, 0, 1, 1, 0, 1, 0, 0] |
构造线性方程组A * X = B,在GF(2)域上使用高斯消元法解出mask,
EXP:
import binascii |
小蓝鲨的RSA密文
题目描述:”小蓝鲨是海洋数学天才,它最近正在深耕RSA领域。你嗤之以鼻,心想RSA不是最基础的密码学知识吗?于是你信誓旦旦的跑到小蓝鲨面前告诉它你已经完全掌握了RSA,并宣称所有的RSA题目你都能做出来。 小蓝鲨意味深长的看了你一眼,并出了一道RSA来考考你。现在,该你向它证明你的实力了。”
打开.py文件,
import json, secrets |
模数N(两512位素数乘积)过大,而m(AES-key)只有128位
我们可以采用爆破low_bits,遍历0 - 65535的所有可能值,构造完整的a2;再求解三次方程m^3 + a2*m^2 + a1*m + (a0 - c) = 0;用二分查找找到m;最后,用找到的密钥m解密ct即可得到flag。
EXP:
import sys |
baby_math
题目描述:死去的记忆突然被唤醒了
打开:
from Crypto.Util.number import bytes_to_long |
给出a * cos(x) + b * sin(x) = enc,此为背包问题的变种
可以利用```LLL算法``,构造格,构造矩阵使得目标向量为格的一个短向量,利用格基约减求解。
EXP:
from Crypto.Util.number import long_to_bytes |
小蓝鲨的费马谜题
题目描述:小蓝鲨在一次网络探险中发现了一个神秘的加密系统。他发现这个系统好像使用了费马小定理来保护重要信息,但是又好像不太一样。小蓝鲨设法截获了系统的加密输出,但不知道如何解密,你可以帮帮它吗?
打开,还有25KB的output.txt:
import random |
根据给定的hint:H(a,b) = a ^ (p - 1) + b ^ (p - 1) mod n
与费马小定理b ^ (p - 1) = c ^ (p - 1) = 1 (mod p)
得出p = gcd(H(a,b) - H(a , c), n)
所以,EXP:
import re |